If you use ReFS for your Veeam repositories it makes sense to monitor the Windows Event Log for error ID 133 (“The file system detected a checksum error and was not able to correct it. The name of the file or folder is…”).
ReFS feature Data Integrity Streams validates and maintains data integrity using checksums. In case of silent data corruption, it will generate the mentioned event log record.
Here is a simple solution how you can set up an alerting rule:
- download blat.exe (command line utility that sends eMail using SMTP)
- create a folder (eg. C:\temp\alert) on the server holding the ReFS repositories
- copy blat.exe into the folder folder
- create an alert.bat file with the following content:
C:\temp\alert\blat.exe -to <recipient> -server <your_smtp_server> -port 25 -f <sender_address> -subject “Attention, found Error ID 133 ReFS Data Corruption in Eventlog”
Next, open the Windows Task Scheduler and create a new task with the following settings:
General Tab:
- Name: Alert Error 133
- Security options: Change User or Group -> NT AUTHORITY\SYSTEM
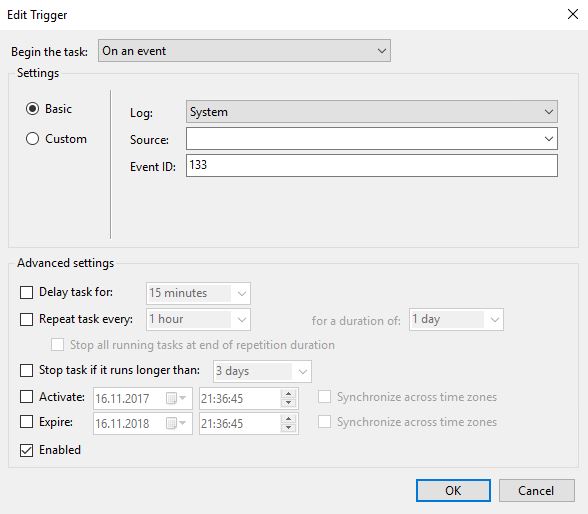
Triggers Tab:
- NEW… -> Begin the task “On an event”
- Basic
- Log: System
- Event ID: 133
- activate “Enabled”
- Action: “Start a program”
- Program\script: specify the path to your alert.bat file
Check the other available options if useful for you and save the task.
How can I check if the alerting rule operates as expected?
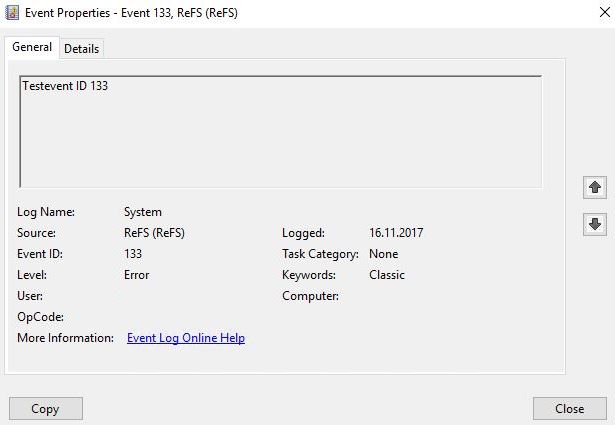
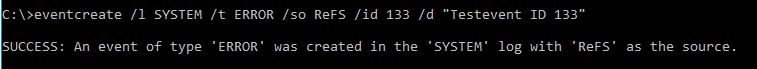
You can generate a test event with ID 133 using the eventcreate command utility.
Open a command prompt and enter the following command:
eventcreate /l SYSTEM /t ERROR /so ReFS /id 133 /d “Testevent ID 133”
Check the System event log and you will hopefully find the created test event ID 133:
When the monitoring task is working as expected you should find a mail with the alert in your inbox.